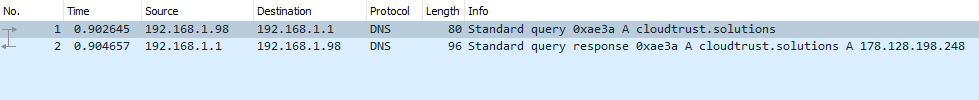
Even if you are visiting a site using HTTPS, your DNS query is sent over an unencrypted connection. That means that even if you are browsing https://cloudtrust.solutions, anyone listening to packets on the network knows you are attempting to visit cloudtrust.solutions.
To prevent this problem, CloudTrust offers DNS resolution over an HTTPS endpoint. If you build a mobile application, browser, operating system, IoT device or router, you can choose for your users to use the DNS over HTTPS endpoint instead of sending DNS queries over plaintext for increased security and privacy of your users.
CloudTrust public DNS provides the following distinct DoH APIs at these endpoints:
Protocol - DNS-over-HTTPS (DoH)
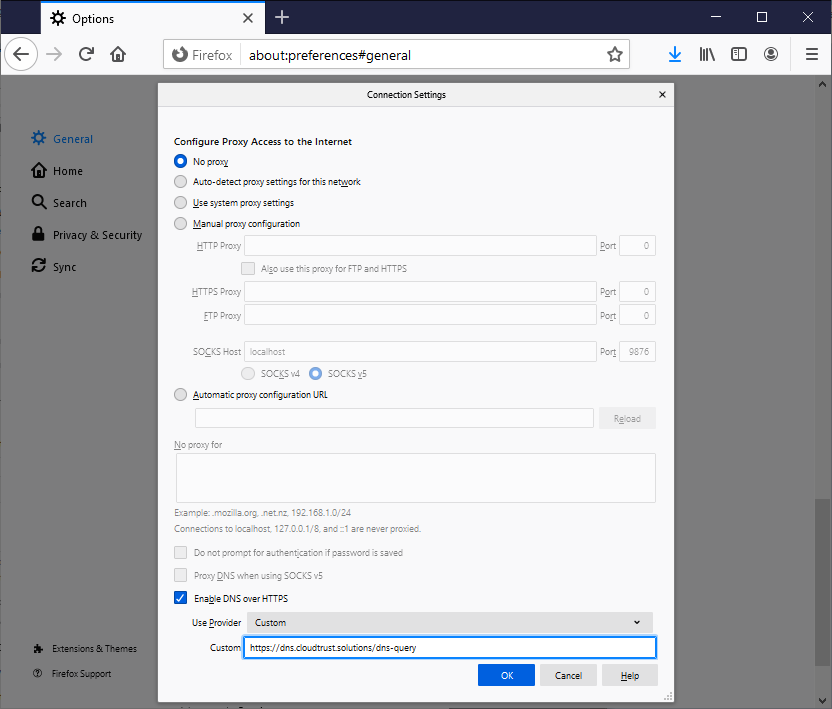
https://dns.cloudtrust.solutions/dns-query
Protocol - Oblivious DoH target
sdns://BQcAAAAAAAAAGGRucy5jbG91ZHRydXN0LnNvbHV0aW9ucwlkbnMtcXVlcnk
DNSSEC
No filter
No logs
Protocol - Oblivious DoH relay
sdns://hQcAAAAAAAAADzIwNy4xNTQuMjM4LjE1NAAYZG5zLmNsb3VkdHJ1c3Quc29sdXRpb25zCi9kbnMtcXVlcnk
No logs
Protocol - DNS-over-HTTPS (DoH)
IPv4 stamp
sdns://AgcAAAAAAAAADzIwNy4xNTQuMjM4LjE1NAAYZG5zLmNsb3VkdHJ1c3Quc29sdXRpb25zCi9kbnMtcXVlcnk
DNSSEC
No filter
No logs
IPv6 stamp
sdns://AgcAAAAAAAAAFFs2NDpmZjliOjpjZjlhOmVlOWFdABhkbnMuY2xvdWR0cnVzdC5zb2x1dGlvbnMKL2Rucy1xdWVyeQ
DNSSEC
No filter
No logs
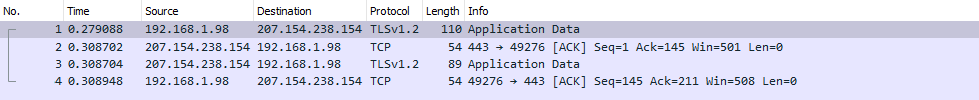
CloudTrust public DNS does not support insecure http: URLs for API calls. No authentication is required to send requests to this API. CloudTrust's DNS over HTTPS resolver supports TLS 1.2 and TLS 1.3.
The POST method is only supported for the RFC 8484 API and uses a binary DNS message with Content-Type application/dns-message in the request body and in the DoH HTTP response.
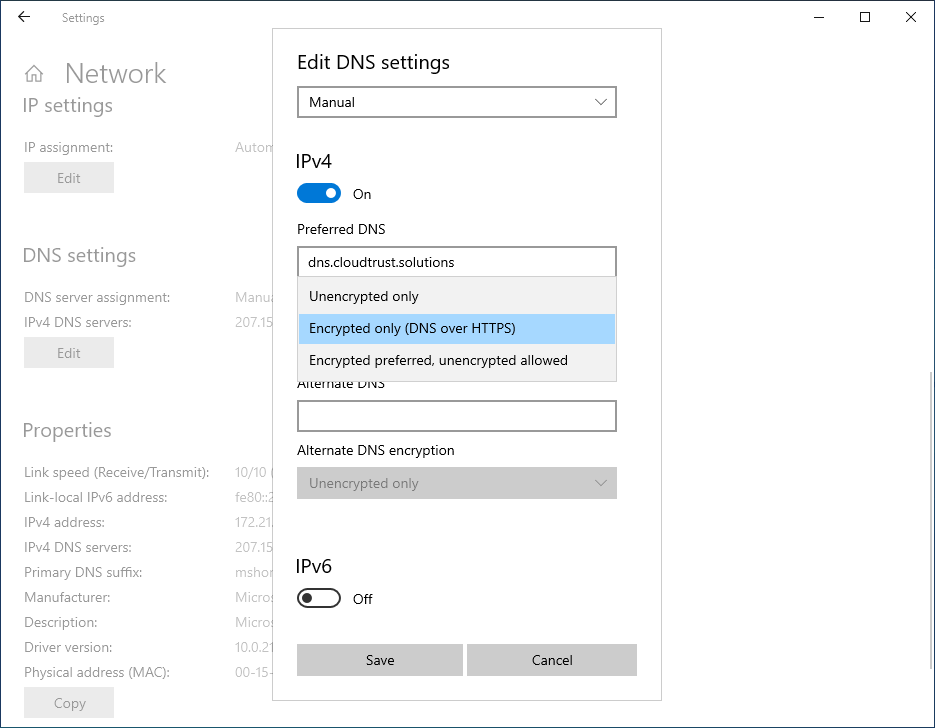
Keep your DNS queries private by using DNS over HTTPS (DoH) in supporting OS, operating systems. Your OS's DNS traffic becomes encrypted to remain private and unmodified.
To prevent this problem, CloudTrust offers DNS resolution over an HTTPS endpoint. If you build a mobile application, browser, operating system, IoT device or router, you can choose for your users to use the DNS over HTTPS endpoint instead of sending DNS queries over plaintext for increased security and privacy of your users.
CloudTrust public DNS provides the following distinct DoH APIs at these endpoints:
- https://dns.cloudtrust.solutions/dns-query – RFC 8484 (POST)
- https://dns.cloudtrust.solutions/resolve? – JSON API (GET)
CloudTrust public DNS does not support insecure http: URLs for API calls. No authentication is required to send requests to this API. CloudTrust's DNS over HTTPS resolver supports TLS 1.2 and TLS 1.3.
The POST method is only supported for the RFC 8484 API and uses a binary DNS message with Content-Type application/dns-message in the request body and in the DoH HTTP response.
GDPR and CloudTrust DoH
CloudTrust supports the GDPR and all CloudTrust services – including DNS over HTTPS service, is provided by Europe Region – comply with its provisions. Not only is the GDPR an important step in protecting the fundamental right of privacy for European citizens, it has raised the bar for data protection, security and compliance in the industry.Using HTTPS DoH, not just TLS encryption, has some practical benefits
- Widely available and well-supported HTTPS APIs simplify implementation for both CloudTrust public DNS itself and potential clients.
- An HTTPS service provides web apps with access to all DNS record types, avoiding the limitations of existing browser and OS DNS APIs, which generally support only host-to-address lookups.
- Clients that implement QUIC UDP-based HTTPS support can avoid problems like head-of-line blocking that can occur when using TCP transport.
Protect your DNS traffic with DoH
Keep your DNS queries private by using DNS over HTTPS (DoH) in supporting web browsers. Your browser's DNS traffic becomes encrypted to remain private and unmodified.
Keep your DNS queries private by using DNS over HTTPS (DoH) in supporting OS, operating systems. Your OS's DNS traffic becomes encrypted to remain private and unmodified.
Application operations, DevOps
In the case where a Cloud service provider hosts a solution implemented in a micro-service architecture, for example, and this service needs to communicate with external service points not under its own control, we have to face the risk of misuse of a DNS redirect. No matter how thorough the design and implementation, even if we have created a logical and physical system design, the trust of the DNS databases is important. We need to be prepared for such cases and scenarios when designing the application and have a dedicated or trusted DNS resolution service in the live infrastructure, as well as use an HTTPS based DNS query mechanism in our application or for the operating systems/containers used.Related network resources and solutions
- Telemetry services are available at https://cloudtrust.solutions/telemetry/
- Speedtest solutions available at https://cloudtrust.solutions/speedtest/
- Connect your Windows or Mac to CloudTrust VPN Edge at https://cloudtrust.solutions/edge/
